SecVision system is designed for collecting, registering, correlating and analysing of data from various sources of events occurring within the information structure. The system compares the data of threats, vulnerabilities, changes in information resources.
Purposes of the system:
- Providing actual information on security of information resources in real-time regime
- Fast and accurate threat detection and warning
- Improving productivity of analysts, to improve the management of incidents
- Improving of security measures
Possibilities:
- Review of events in real time
- Notification of deviations from normal behavior
- Notification of unusual user activity
- Automated reports for compliance with regulations and standards
SecVision system collects all log-sets from all devices and software systems of your network; archives copies of all of the data; processes the logs in real time; generates alerts when it detects suspicious behavior of users, of software systems or of devices.
Administrators, using the central management console, can query the entire volume of stored data, as well as produce detailed investigation of incidents.
Powerful analytical module converts the total mass of unstructured raw data into structured information, formalizing what is going to help the administrators in the areas of:
- Simplifying of compliance with industry regulations
- Improving safety and reducing risks
- Optimizing the functioning of IT-infrastructure
The system provides an effective data collection and analysis of system logs. This contributes to a better understanding of state security, compliance with technical standards and organizational performance in the current time or during a certain interval.
The system receives data from:
- network devices
- operating systems
- databases
- enterprise applications
Scheme of the systems work:
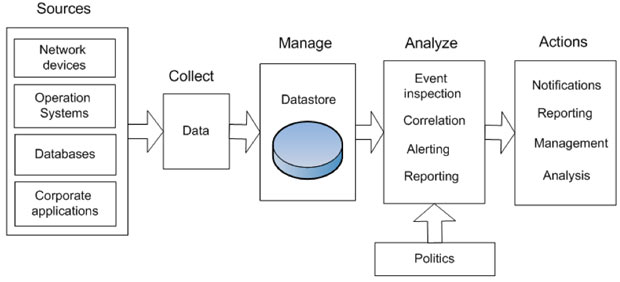
- Retrieving the log data from all sources
- Data accumulation in warehouses
- Structuring of the accumulated data
- Analysis of data by policies
- Generating alerts, retrospective analysis, resource management
Components of the complex:
- Storage of original data
- Storage of structured data
- Module analytical analysis
- Generator of alerts
- Report generator
- Management Console complex
Features of the complex:
- The large number of predefined policies and reports
- Archiving of raw data in an unmodified state, which prevents distortion of the original data
- Retrieving the log data without installing agents on the data sources
- Integration with Active Directory
- Graphical and textual representations of data and reports in various sections
- Possibility of distribution of system parts on different servers to optimize performance
- Centralized management of complex
- Ability to configure extraction the log data for unknown types of devices/logs
- User roles for the permission distribution of system users.